Cyber Security Companies in Pune: How to Select the Right Partner (2025)
December 14, 2025|9:51 AM
Unlock Your Digital Potential
Whether it’s IT operations, cloud migration, or AI-driven innovation – let’s explore how we can support your success.
December 14, 2025|9:51 AM
Whether it’s IT operations, cloud migration, or AI-driven innovation – let’s explore how we can support your success.

Pune has evolved into a major manufacturing and IT hub, creating unique cybersecurity challenges. Local industrial operations face threats that span both traditional IT systems and operational technology (OT) environments. The convergence of these worlds requires specialized expertise that many cybersecurity companies in Pune are now developing.
When evaluating security services companies in Pune, a structured approach ensures you select a partner who understands your specific industrial requirements. The following scorecard provides a comprehensive framework for assessment.

| Evaluation Criteria | Key Questions | Importance (1-5) |
| Hybrid Environment Capability | Can they secure both on-premises and cloud environments with consistent governance? | 5 |
| OT/Plant Experience | Do they have specific experience with industrial control systems and operational technology? | 5 |
| Incident Response | What is their MTTR (Mean Time to Respond) for critical incidents? Do they have 24/7 coverage? | 4 |
| Change Management | How do they handle security updates in production environments? Do they respect maintenance windows? | 4 |
| Visual Inspection Security | Can they secure AI-powered visual inspection systems at the edge? | 3 |
| Compliance Expertise | Do they understand industry-specific regulations and compliance requirements? | 4 |
| Local Presence | Do they have local teams in Pune who can respond quickly to on-site issues? | 3 |
Contact Opsio for a customized evaluation framework tailored to your specific industrial security requirements.
Managed Detection and Response (MDR) and Security Operations Center (SOC) services form the backbone of effective cybersecurity. For industrial environments, these services must be tailored to accommodate operational constraints.

Continuous monitoring with context-aware alerts that understand normal industrial operations vs. actual threats. Reduces false positives by 40-70%.
Response procedures that respect production constraints and safety requirements. Includes pre-approved playbooks for common scenarios.
Industry-specific threat intelligence focused on manufacturing, engineering, and industrial control systems targeting Pune businesses.
Visual inspection systems powered by AI are transforming quality control in manufacturing, but they introduce unique security challenges that many cyber security companies in Pune are still learning to address.

“Most visual inspection projects stall due to inconsistent data capture, labeling bottlenecks, drift, integration gaps, and weak operational ownership/security at the edge.”

Leading cyber security companies in Pune are implementing these proven approaches to secure industrial environments while maintaining operational integrity.

Standardizing data capture procedures ensures consistent training data for AI models. The “golden sample” approach establishes verified reference points that can be used to validate system integrity and detect potential security compromises.
Implementing MLOps practices provides governance over the entire machine learning lifecycle. Regular drift monitoring detects when models begin to deviate from expected behavior, which could indicate either natural evolution or security compromise. Strict model versioning ensures that only authorized models are deployed to production.
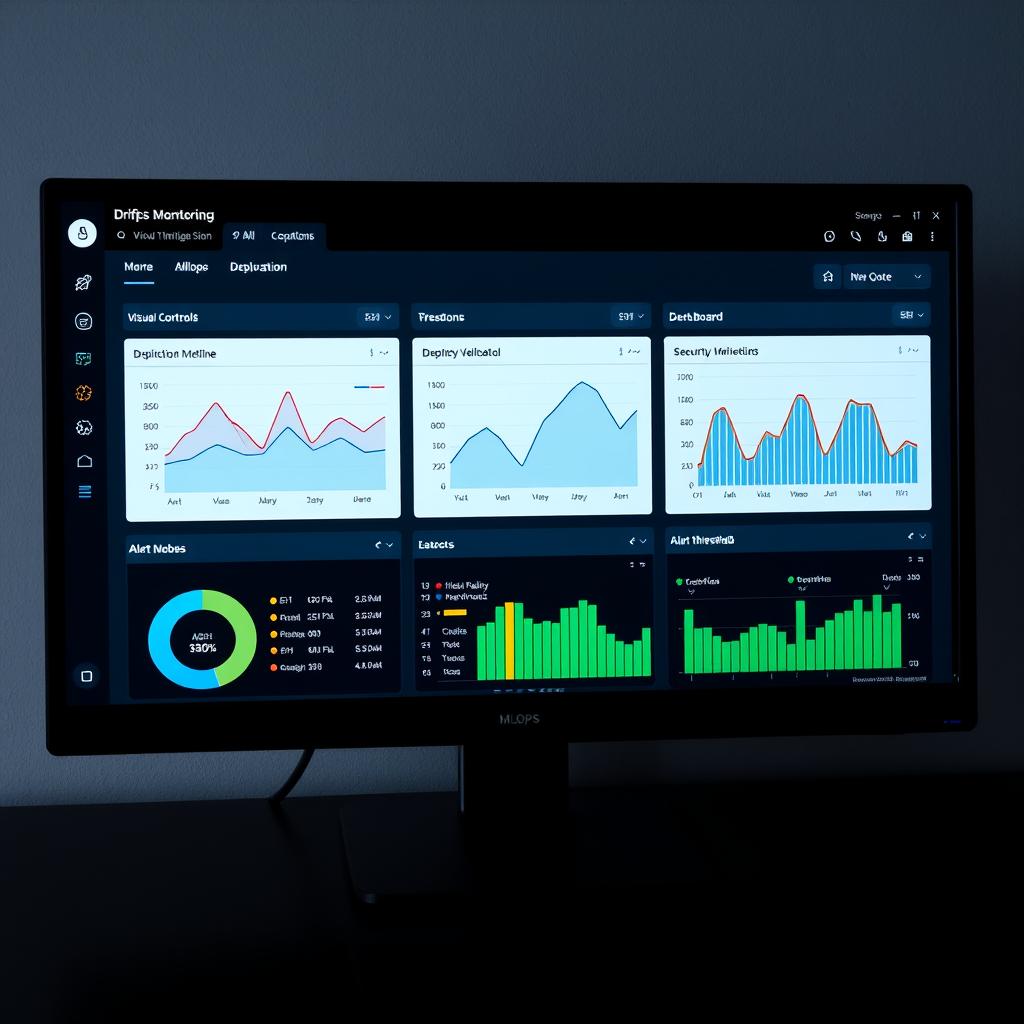
Edge devices running visual inspection systems require specialized security approaches that respect operational constraints:
| Security Measure | Implementation Approach | Operational Benefit |
| Network Segmentation | Isolate visual inspection systems in their own network segment with controlled access points | Prevents lateral movement while maintaining necessary operational connections |
| Least Privilege Access | Implement role-based access control with just-in-time privilege elevation | Reduces attack surface while ensuring maintenance access when needed |
| Scheduled Patch Windows | Coordinate security updates with planned maintenance downtime | Maintains security without disrupting production schedules |
| Allowlisting | Permit only authorized applications and processes to run on edge devices | Prevents unauthorized software while maintaining system stability |
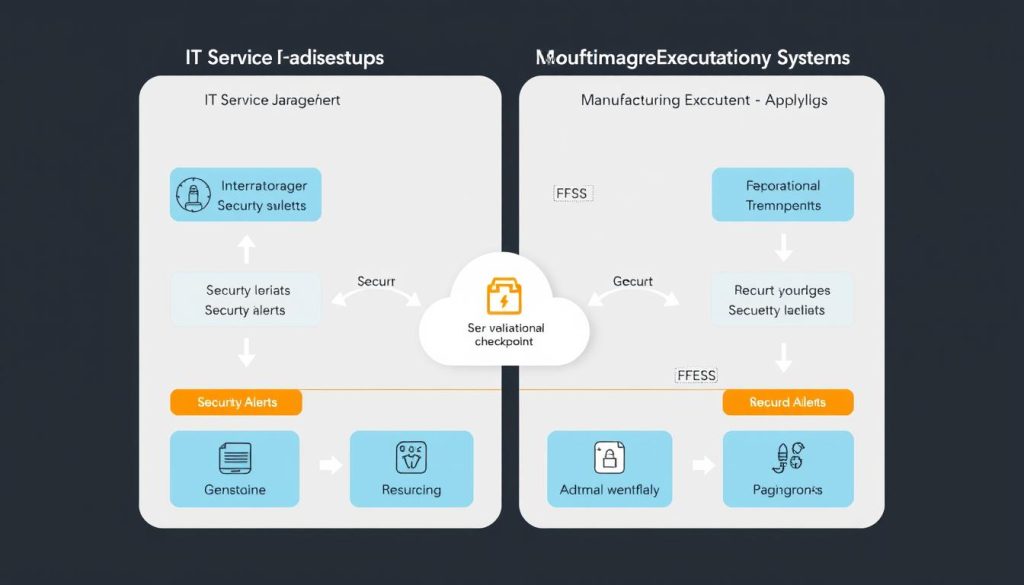
Integrating security workflows with IT Service Management (ITSM) and Manufacturing Execution Systems (MES) creates closed-loop processes that ensure security events are properly handled within operational constraints. This approach bridges the gap between IT and OT teams, ensuring coordinated responses.

Yes—if they design change windows, segmentation, and monitoring that respect uptime and safety constraints. Look for providers with specific experience in industrial environments who understand that production continuity is the priority. The best cyber security companies in Pune will have documented procedures for working within maintenance windows and emergency protocols that don’t compromise safety or production.
Most stall due to inconsistent data capture, labeling bottlenecks, drift, integration gaps, and weak operational ownership/security at the edge. Successful implementations require standardized operating procedures for data capture, efficient labeling workflows, regular model monitoring, proper integration with existing systems, and clear ownership of both security and operational aspects.
Assess their ability to provide consistent security controls and governance across both on-premises and cloud environments. Ask for specific examples of hybrid deployments, their approach to identity management across environments, and how they handle data protection for workloads that span both domains. The best providers will have reference architectures and case studies demonstrating successful hybrid security implementations.
Choosing among cyber security companies in Pune requires careful evaluation of their ability to bridge the IT/OT divide while respecting operational constraints. The right partner will understand both the technical security requirements and the business imperatives of industrial operations. They’ll provide solutions that protect your digital assets without compromising production or safety.
By applying the evaluation framework and implementation approaches outlined in this guide, you can select a cybersecurity partner who will help secure your operations today while enabling your digital transformation journey for tomorrow.

Contact Opsio today to discuss your specific security requirements and how we can help protect your operations while enabling digital transformation.